Encryption
Encryption is a data protection technique that uses mathematical algorithms to scramble information into an unreadable format (ciphertext) that can only be reverted to its original state (decrypted) using an encryption key.
PII, or personally identifiable information, encompasses data elements that, when taken alone or combined, can single out an individual. Due to the nature of this information, its sensitivity, and regulatory requirements, it’s crucial to secure it. Encryption, along with tokenization, is one of the best ways to protect PII.
Of all types of encryption, application-level encryption is one of the most effective ways of protecting sensitive data because the application controls the encryption and decryption processes, while the database doesn’t even hold the encryption keys. This means that even if a malicious actor gains access to the database, they won’t be able to decrypt the data it contains.
Instead of encrypting all data that an application uses, it makes sense to focus on encrypting PII for the following reasons:
- There are operational limitations to encryption, so we need to be selective in what we encrypt.
- Encryption deidentifies data, making PII indecipherable to attackers.
- If data is stolen, we prevent harming customers and avoid stiff fines imposed by the GDPR and other data privacy laws.
Here are the operational limitations to encryption that you should know about:
- Cryptographic keys should be secure and never leave their designated service, such as a data privacy vault or a key management system (KMS).
- When a data element is encrypted, it’s harder to search over it. Searchable encryption exists, but implementing it requires extra effort.
- Robust encryption may cost more in disk and memory space.
- Encryption may introduce a slight performance hit.
Encryption pitfalls that can lead to data vulnerabilities
In data security, good intentions aren’t enough. Encryption missteps can leave sensitive data vulnerable. Here are 5 common pitfalls in data encryption that could expose sensitive data:
- Wrong encryption algorithm. Choosing the right encryption algorithm is crucial. The WEP Wi-Fi security failure underscores the need for strong, use-case-appropriate algorithms.
- Key management. Effective key management begins with secure storage, protection, and regular key rotation. This becomes increasingly challenging at scale. Advanced methods, such as split keys in MPC systems (as employed by Coinbase and Binance), add layers of complexity.
- Wrong encryption mode. Zoom’s encryption fiasco taught us that not all methods are equal. They chose ECB, a weaker block cipher mode, over more secure options like CBC. Don’t be like Zoom: choose wisely.
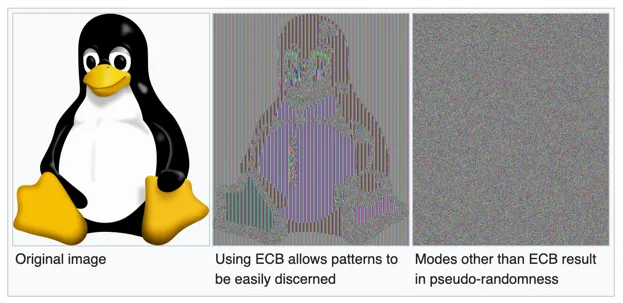 (Image courtesy of Wikipedia)
(Image courtesy of Wikipedia) - Padding oversights. Padding is crucial for encryption yet is often overlooked. Inadequate padding can weaken encryption, and incorrect padding might leak key details, opening doors to attacks like the notorious padding oracle.
- Side-channel timing attacks. These sophisticated threats exploit execution time variations in your encryption system, leaking critical information. Writing robust code to resist such attacks is essential, although challenging.
Don’t fall victim to encryption pitfalls: embrace expertise, best practices, and continuous learning. Let’s prioritize smart encryption practices for truly effective security.